Reading Time: 5 minutesOleg Brodt works at Deutsche Telekom Innovation Labs in Israel. He comes from the small city called Beersheba, also spelled Beer-Sheva, which also is the largest city in the Negev desert of southern Israel. In the end of October this year he spoke at Masters&Robots Conference in Warsaw, and I would like to present some of the highlights of his speech on cyber security.

1. Beersheba – as a Cyber Security Center of Israel
Israeli government decided that Beersheba is going to be a cyber security capital of Israel (being more than 4 times smaller than Warsaw). Therefore, all the cyber security units of military and other agencies were moved to this city. That is what made a great impact on Beersheba’s development and stimulated the inflow of human capital into the city. Nowadays there are 40 multinational companies located in Beersheba. There are also many accelerators, incubators, around 100 Start-Ups and the Ben-Gurion University, which is the only university in Israel offering a cyber security degree. Generally, there are around 400 Start-Ups focused on cyber security in Israel, furthermore, the country attracts 15% of global venture capital financing of cyber security projects.

Beersheba 2007

Beersheba 2017
2. Cyber Security Kids – Israeli Programs for Talented Pupils
In Israel children, who are good at math and IT, have a chance to become a part of the educational programs, which are aimed to prepare human resources for Israeli military units. Those are usually kids, who go to 9th grade. If the kid is cherrypicked, he or she attends the after school classes on cyber security twice a week during four years of high school and after this, he or she joins the army unit.
By the time a child finishes a school, he or she is already an expert in cyber security. Moreover, there is a 6-months gap between the kid finishes school studies and joins the military agency, and during that gap, a kid already works on military CS projects in IT labs. Those are the lowest qualified workers in Israeli IT Labs. The IT labs are being headed by professor Yuval Elovici, who is a known academic figure in the field of CS.

3. There are Different Kinds of Attackers in CS
- Kids (“Script Kiddies”) – just children, who are bored, they have spare time and technical skills to hack you. They have some basic knowledge, and start to play around with CS, however, they are lowly qualified and normally can not do a lot of harm. Moreover, kids are hacking for “FUN”, there is no real money interest in it.
- State Actors – governments, which hack each other or specific targets. They are extremely highly qualified, and if you are the target – it will be very difficult to defend. Also, they have “unlimited resources” to hack you, which means they are very dangerous and if they really want to hack you, it is a question of time.
- Cybercriminals – revenue driven hackers, who aim to get a financial benefit from you.
- Hacktivism – is the subversive use of computers and computer networks to promote a political agenda or a social change. Perhaps the most prolific and well known hacktivist group, Anonymous has been prominent and prevalent in many major online hacks over the past decade.
- Terror Organizations – not very active in the field of CS yet, but are increasing their activity gradually.
/hacker-Gu-577f9e9d3df78c1e1fb0b9c4.jpg)

4. Financial Models of Attackers
There are also different ways attackers might harm you and there are some of them:
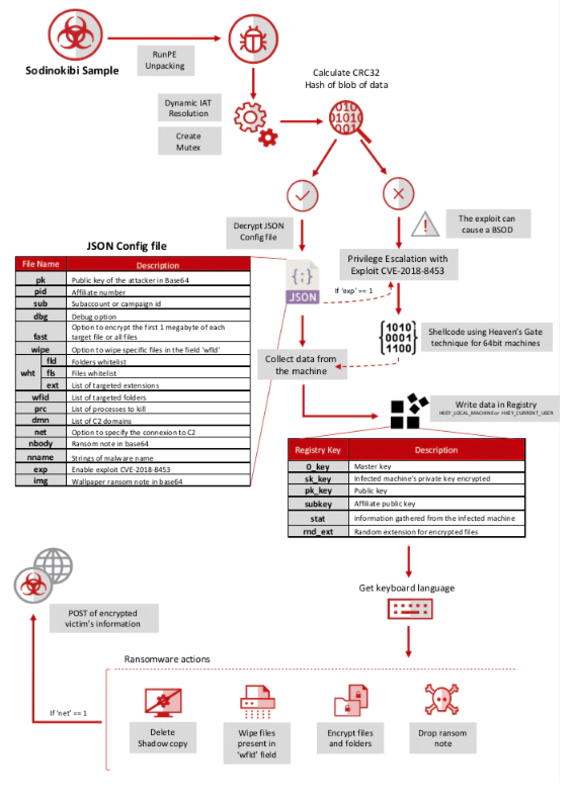
- Ransomware – a type of malicious software from cryptovirology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. While some simple ransomware may lock the system in a way which is not difficult for a knowledgeable person to reverse, more advanced malware uses a technique called cryptoviral extortion, in which it encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them.
- DDOS-as-a-Service – a new service in the Darknet. If you want to attack your competitor in the internet (for example internet shop), you order such a service in the Darknet from qualified hackers, and than they attack the e-commerce platform of your competitor in a way that it gets too many requests and falls offline.
- Crypto-Hacks – is something relatively new, and means that hackers attack bitcoins exchangers in order to still their money.
- Darkweb hacking services – there are even whole price lists for certain violations in the Darkweb. For example, how much does it cost to buy a thousand credit cards, or to hack somebody’s Facebook account.

5. It Is Not Personal – When Hacking You is a Business
- The hackers, who attack you because of financial motivation are interested only in getting the money. They really do not care who you are, they are not hacking you because you are you, they are hacking you because of your resources. And the most popular way to hack during last two years is ransomware. Due to its “commonness”, there starts to arise a commoditization of the services connected to ransomware, so to say. In other words, hackers, who attack you with ransomware have support centers! So, for example, if you get hacked, and your entire organization data in currently encrypted, you get a message that you have to pay a ransom in bitcoins, but you do not know what actually bitcoin is – you may address hackers’ customer service for help. Yes, you get a phone number on your screen, and if you call on this number – a nice customer service representative guide you through the whole process. Sounds nice, hah?
- Organizations, which are specialized in negotiations with hackers arise. For example: you are being hacked, and the attacker wants you to pay 5000$ ransom for your files. But how can you know that after the transfer of the money the files will be released? That is where negotiations companies come into play. First, they try to establish a reputation of the hacker – they ask him questions like: “How do I know that you are not going to publish my files in the Darkweb?” or “How do I know that you are not going to sell my files to other organizations?” And what happens next is something surprising – hackers give lists of “previous customers” (people or organizations, which were hacked by them before) to convince the victim that the deal is safe. They also propose to refer to those “customers” to get a recommendation. So there exists so-called recommendation base for hackers, in which new negotiations companies are specialized.
Sources:
- https://en.wikipedia.org/wiki/Ransomware
- https://en.wikipedia.org/wiki/Beersheba
- Oleg’s Brodt Speech at Masters&Robots Conference in Warsaw (26-27 October 2017)






/hacker-Gu-577f9e9d3df78c1e1fb0b9c4.jpg)

