If you use the software, such as voice assistants of the largest companies, you should be aware, as scientists discovered a new type of hacker attack!
The attack exploits the sensitivity of microphones using micro-electro-mechanical systems (MEMS). Microscopic MEMS elements react to light as if it were sound. Although researchers have tested the possibility of hacking only Siri, Alexa, Google Assistant, Facebook and a limited number of tablets and phones, they believe that all devices using MEMS microphones are vulnerable to this threat.
Below you can find a video showing how exactly this procedure works:
https://www.youtube.com/watch?time_continue=29&v=iK2PtdQs77c&feature=emb_title
The attack is based on the idea of exchanging the sound with a low-power laser beam directed at the device. Basically the lasers trick the microphones into making electrical signals as if they’re hearing someone’s voice. It works even from the distance of 110m and can be executed from another building, through glass windows or doors. It can be really dangerous as some people do not use the required authorization feature for certain commands so that hackers are able to open smart garage doors, order stuff from Amazon on your cost or even start your vehicle.
Researchers who discovered this dangerous feature claim that the cost of producing a device that could hack any voice assistant, based on MEMS microphone, is about $400 including $340 laser driver, a $20 laser pointer and a $25 sound amplifier. The low costs and simplicity of using it, in this case, are not an advantage, as it makes it possible for almost anyone to make such a device at home, unfortunately for criminals as well. 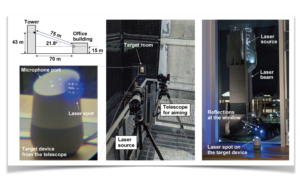
To protect your smart household I would highly recommend setting as many passwords as possible when it comes to the security of your voice assistant, moreover to place it in a part of your house which is not visible from outdoors.
If you would like to find out more details on how exactly this hacker attack works, you can visit the website devoted to this solution:
https://lightcommands.com
sources:
https://lightcommands.com
https://www.cnet.com/news/lasers-can-seemingly-hack-alexa-google-home-and-siri
https://mlodytechnik.pl/news/29884-badacze-hakuja-siri-alexe-i-google-home-za-pomoca-wiazek-laserowych