Have you ever heard “No!” from your parents when asking for a pet? Are you having a busy life and cannot afford spending enough time with a pet? Do you feel lonely in your apartment with no fluffy tale? Qoobo can be a solution for you.
According to Engadget, at CEATEC, the Japanese company called “Yukai Engineering” unveiled its latest wacky product, the Qoobo “tail therapy” robot. This is essentially a cushion with a realistic cat tail that reacts to stroking and patting, such that it’s able to comfort its “owner” like a real pet would simply through tail wagging.
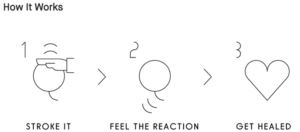
According to creators of Qoobo, it is a robotic pillow with a tail intended to provide a sense of comfort to users. When caressed, it waves gently. When rubbed, it swings playfully. And, it occasionally wags just to say hello. Qoobo was designed for communication that warms your heart the way animals do. “Through trial and error, we developed a mechanism that closely mimics the flexible and elegant movements of an animal. We selected different materials for various parts of the robot to enhance the movements and the tail’s appearance. We also made it durable to allow for use in various environments” – say Yukai Engineering.
The story of Qoobo is very ordinary: the idea of the pillow originates from one of Yukai Engineering’s employees. The designer had a cat, but since the apartment she moved into didn’t allow pets, she had to leave her cat with her parents. This inspired her to come up with a lifelike pet substitute that would make her feel better whenever she thought of her cat.
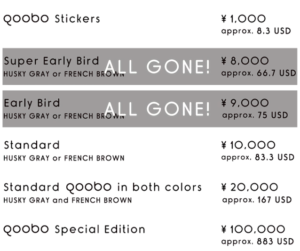
According to The Verge, Qoobo is expected to cost around $100 when it launches in June 2018. Like with its adorable Bocco robot that was delivered with Kickstarter, the company is hoping to launch Qoobo with the help of a crowdfunding platform too. It’ll have an eight-hour battery life with USB charging, and will come in two colors: Husky gray and French brown.
Now you can back Qoobo at the page of the project at Kickstarter platform, and starting from $83 you can order a pillow and expect the delivery by June 2018.
People, who have already “touched” Qoobo say, that they were surprised by how realistic the tail moved, especially with how its wagging intensity increased as they petted it harder. Interestingly, the stroking detection is mostly done with just one accelerometer inside the body, according to CEO Shunsuke Aoki. He added that despite the cat-like appearance, the realistic tail movement is actually based on research on both cat and dog behavior.
Being a former dog owner, I must say, that I hardly imagine how a pillow can replace a real pet. But it looks like robots never die, unlike our pets…
Sources:
https://www.theverge.com/2017/10/5/16431118/qoobo-yukai-engineering-cat-tail-wagging-robot
https://www.kickstarter.com/projects/1477302345/qoobo?ref=thanks_link
https://www.engadget.com/2017/10/04/qoobo-cat-tail-cushion-therapy-robot/






/hacker-Gu-577f9e9d3df78c1e1fb0b9c4.jpg)